
The ISO2700x series is updated. As you probably know, the ISO 27002 has been refreshed, and the ISO/IEC 27001 is the following1. The main consequence of these updates is for the ISO/IEC 27001 certified companies. An update of an ISO standard involves, for the certified companies, being in compliance with the versions of the new standards. For a major change, companies usually have three years to make the transition. In our context of change, it would probably be reduced to two years.
There is good news! The major changes are a merge of redundant controls and a split of too heavy ones. Nevertheless, the transition to the new version should be anticipated as much as possible.
The new version of ISO/IEC 27002 reflects the gain of maturity in last year’s cybersecurity field. If you read it carefully, you’ll see subtle improvements: risk-centric and process-oriented putting people in the Information Security Management System (ISMS) heart. This is a perfect alignment with the ISO global vision.
Consequently, your ISMS should already be lined up with this new version except for Statement of Applicability (SoA). At least, it could be good to conduct a gap analysis to realign the SoA with the iso 27002 and confirm that the ISMS covers correctly all the controls. This gap analysis is a good opportunity to do the annual review and confirm the security objectives.
It is not necessary to give figures on the number of remaining security measures, as many of our colleagues have already addressed this subject from this perspective. Just remember that there is no deletion of security measures, but a merging of some and a split of others. This is a useful update to clarify both the objectives to be achieved and how to achieve them. New security topics and measures have been added to address current and up-to-date information security issues.¨
To understand the changes and their scope, let us analyse them through four themes:
- People
- Incident management
- Suppliers
Main Changes highlighted
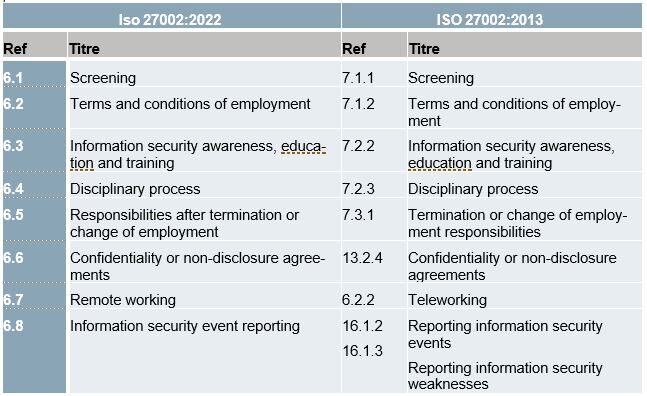
Everyone who interacts with the information system should act for information security and data protection. Employees and suppliers share the same responsibilities. Everyone in the company, regardless of their role and function, must be able to detect and report security events, share information within the confidentiality guidelines, store documentation on appropriate media, etc. In other words: apply the same security rules. For this purpose, the company needs to review the processes covering the entire life cycle of people in the company, from recruitment to promotion or change of position to departure. It is also clear that the overall HR process should be the same regardless of the employment status of the individuals (contractor or employee) in respect of the applicable regulations.
At the process level, differences in stakeholders, their responsibilities, and the results of the process need to be managed. For example, for a contractor, the information security requirements are in his contract rather than a charter for the employee. The company should list the security requirements and require their third parties to ensure that their employees are continuously aware of and comply with them.
The user, considered an active sensor, is an asset for cyber security. Who is better placed than the user to report security events? The user is often at the forefront. It is therefore important to ensure that everyone can report suspicious events. Procedures, tools and communication channels must be in place. The priority is to give users the keys to detect, identify and report these events. Do not underestimate this evolution of the standard. While, in the previous version, the focus was on the responsibility to report. In the current version, the emphasis is on the means to be deployed and maintained to enable people to identify and report security failures.
Expected benefits
Currently, most companies manage employees and suppliers using distinct processes. Eraneos experts often observe an unequal level of awareness and application of security rules by these two populations, even though they work similarly with tools and data. Pooling these activities through a single process brings efficiency gains, cost savings and reduced risks of error.
Managing security rules and training or awareness content singly and centralising them makes it easier to keep them up to date and ensures that this information is distributed uniformly. Thus, all the people concerned have the same level of information. A rapid increase in the level of security can be observed, thanks to users who are aware of and trained to react.
The risks of data leakage, particularly through negligence or ignorance, are reduced and at the same time, everyone feels responsible for the data they handle and is more careful. As users have better reflexes, security incidents are detected and dealt with more quickly, reducing their impact.
Main changes highlight
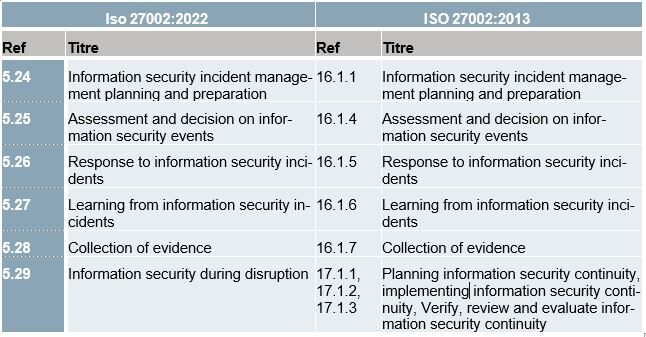
As explained previously, people and skills are a strong pillar of information security, and this is naturally reflected in the incident management process. Only competent and authorised people should deal with security events, and this should be done in the interests of efficiency and risk control. However, both external (including authorities) and internal stakeholders are considered essential to resolving the incident.
This collaboration in incident resolution with external parties, including suppliers, is facilitated by the new structure of this theme: the six safety measures represent each of the steps in the incident management process. The need to establish a process is explicitly recommended by the 5.24 security measure.
Thus, a structure for the incident management process is recommended. A workflow can be easily drawn up, in line with good practice, helping to improve the efficiency of the incident management process between and within organisations. Collaboration between organisations such as customer-supplier and between partners for the resolution of incidents between different companies is made possible.
Expected benefits
Improving the incident management process ensures a gain in efficiency in the incident and crisis processes. The gains can be directly due to a reaction in front of security events faster than usual due to a decision-making process smoother.
Knowing the competencies and maintaining them is also the opportunity to retain the key skills. With a turnover reduced, people have a better knowledge of your company context and communication channel. The exchange between teams is facilitated.
The unique incident management process allows the team to collaborate and act faster and efficiently to reduce the impacts of incidents.
Main changes
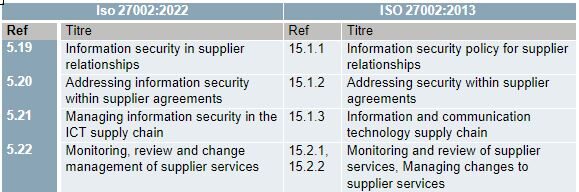
The objective of measure 5.19 - information security in the supply chain, is to "maintain an agreed level of information security in relationships with suppliers" instead of "ensuring the protection of the organisation's assets accessible by suppliers". To achieve this objective, it is not surprising that a process must be designed to manage the risks associated with the use of suppliers' products or services.
The major contribution of the ISO 27002:2022 is the recommendation to implement a process that aims to ensure a strong control of the supplier relationship. The process must cover all stages: from the choice of the service or product in line with the company’s needs, to the termination of the service, considering reversibility, while anticipating the monitoring and control of the conformity of products and services.
Another strength of this version is to make a well-informed decision about choosing a provider: don't choose a standard cloud service for your critical operations because you won't be able to establish a relationship, subscribe to specific services, or even subscribe to superior and appropriate security features for critical service. Although it may seem obvious, writing it into a standard is a good way to get the message across to management.
Expected benefits
Thanks to such a process, the company has control over its suppliers: it is aware of its suppliers, the services they have contracted and their commitments in terms of information security. The execution of contracts can be monitored, and their renewal anticipated. This leads to a rationalisation of suppliers which can reduce the associated costs.
Rationalisation of security costs can be done in a global way: a single supplier can be chosen to deal with a subject. Suppliers with complementary skills can be selected to ensure better coverage of the security level. The result is a better use of the available resources.
Finally, knowing the suppliers and the services and products subscribed to makes it possible to anticipate dependencies on them and to make a reasoned choice on three fundamental levels: the level of service in line with the needs and criticality of the service to be outsourced, the complementarity of the suppliers and the risks in the event of failure of one of them.
How to comply ISO 27002?
In the idea that this standard update is a good opportunity to accelerate, at least a little bit, the information security maturity level with visible benefits, Eraneos suggest conducting a gap analysis and a risk assessment review to build an implementation roadmap.
First start with a gap analysis to have a good idea of the level of conformity regarding the new ISO 27002 standard. Of course, the gap analysis will be focused on main changes like people involvement, processes, and new themes (cloud security, for example). Based on the findings, the priorities can be set up and aligned with the company’s goals and capacities. The gap analysis will allow you to identify the lack of process and determine the main differences that need to be maintained or corrected.
Next, review the risks. As gap analysis output, the security objectives are reviewed and approved. Considering these objectives and the new security controls, the risks are reviewed leading to an update of the risk treatment plan. The Statement of Applicability is updated in accordance with the iso 27002 updates. Finding and risks are prepared to be approved by the management to validate the roadmap and allocate the resources.
Three to six months later, the roadmap is implemented Compliance must be done at the same time as all ongoing projects. It is therefore advisable to carry out the gap analysis and planning early on. This will enable you to obtain the necessary management support, financial resources and expertise in good time.
Anne Lupfer | Senior Consultant Cyber Security | Cyber & Information Risk Specialist
Nils Mörstedt | Senior Consultant Cyber Security & Privacy | Information Security Expert
Engin Akdeniz | Managing Consultant | Cyber | Data Mining | Resilience
Jean Paul Ballerini | Managing Consultant Cyber Security & Privacy | Knowledge Community Leader
Cyber events can quickly destroy corporate assets and damage an organization's carefully built reputation. Is your Cyber Security up to date and do you (still) have your business data under control?
We have compiled reports on our projects, interesting facts from the various competence and customer areas as well as information about our company for you here. To help you find the relevant articles more quickly, you can filter the news articles by topic.
